Flera av våra svenska myndigheter och offentliga verksamheter står idag och vacklar över om de kan spara data i vissa molntjänster. Trots detta ökar konstant behovet att kunna använda Microsoft Teams för att kunna kommunicera med övriga parter med både möten och samarbete. En stor utmaning handlar även om att kunna förvalta en Windowsplattform som idag bygger på molntjänster för att erhålla hög säkerhet med alla dess tjänster. Att idag hantera en Microsoft-infrastruktur utan dessa molntjänster är extremt tidskrävande och kostsam med ett konstant arbete att hänga med i utvecklingen och stänga av de tjänster som har molnkoppling.
Men den här artikeln kommer jag beskriva hur vi kan förhindra datalagring i Microsoft 365 som standard, men även ge möjlighet på ett kontrollerat sätt att lagra viss information i molnet.
Vi kommer tekniskt lösa detta med tjänster inom Microsoft Purview Information Protection och med hjälp av informationsklassificering. ![]()
Vi har precis fått nya funktioner som öppnat helt nya dörrar.
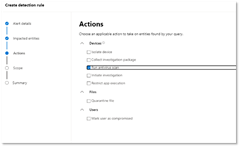
Ett sätt att höja våra användares medveten och stoppa viss typ av information för datalagring i allt ifrån molntjänster, USB minnen och andra lagringsytor är med tekniker inom Data Loss Prevention (DLP). Här kan vi både övervaka, informera och blockera användare när viss typ av information flyttas/lagras utanför organisationens väggar.
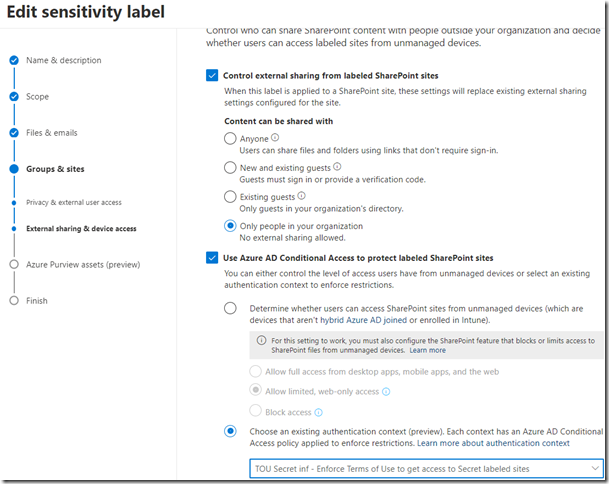
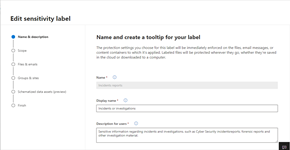
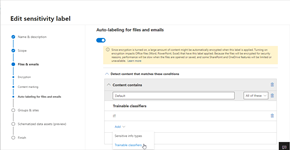
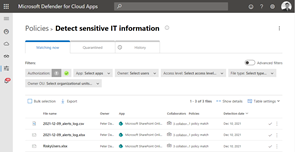
I de flesta fallen handlar det här om viss känslig information som har hårdare krav som innebär kryptering och/eller förhindrande av lagring i osanktionerade (moln)tjänster. Det här löser vi tekniskt genom att identifiera viss typ av information baserat på filernas innehåll eller informationsklassificering (sensitivity labels).
För flera av våra myndigheter är behovet något helt annat. Allt ska som standard blockeras, inget får lagras men det finns undantag för viss information godkänd för datalagring. Detta har varit en teknisk utmaning tidigare, men vi har nu fått teknik som fyller det här syftet.
Vi kan nu låta installera både Microsoft Teams applikationen och OneDrive klienten på våra Windows-enheter inom organisationen. Med hjälp av inbyggt DLP teknik i Windows styr vi så inga filer kan flyttas eller skapas i dessa tjänster. Där emot kan användaren göra ett aktivt val att klassificera en fil manuellt med en viss informationsklassificering som är tillåten att lagras i Microsoft 365. Där efter kan filen flyttas och sparas både i Teams och/eller OneDrive för att synkas till respektive molntjänst.
Tekniskt används ett nytt krav i DLP som handlar om att identifiera om Office filen saknar en sensitivity label. På det sättet kan vi blockera oklassificerade Office filer och övriga klassificerad data som inte är tillåten för molnlagring. Med hjälp av samma DLP-teknik blockerar vi andra filtyper som kan innehålla information för att säkerställa att inte denna lagras i molnet.
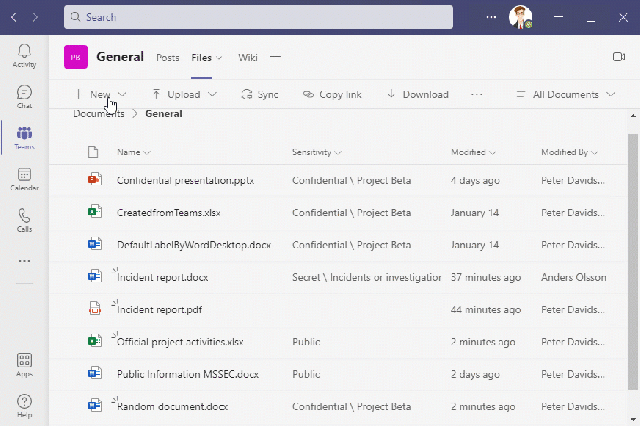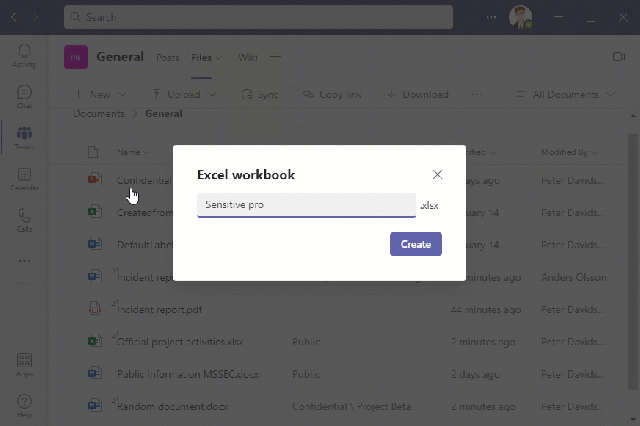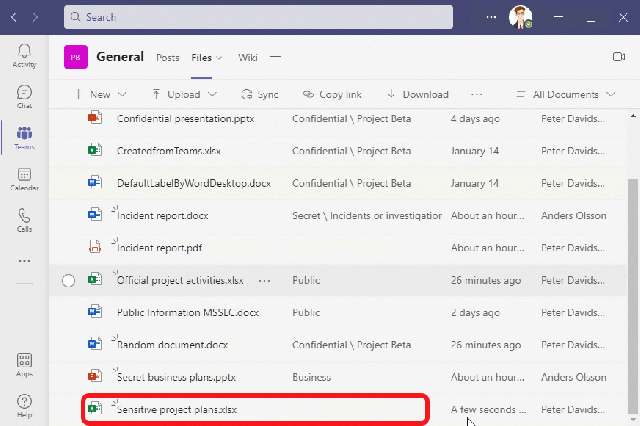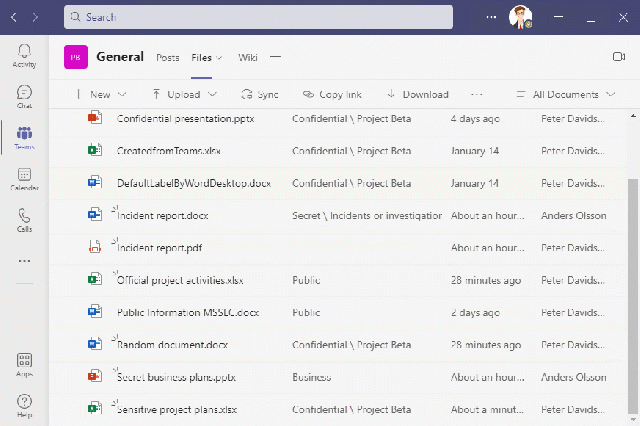
Några exempel på hur det här kan se ut.
Användaren försöker skapa ett Word dokument i OneDrive, vilket blockas av EndPoint DLP i Windows. Användaren tar istället en excel-fil som är klassificerad (med en definierad label) som är godkänd för datalagring som kopieras till OneDrive (och synkas till molnet).
I nästa exempel visar vi hur ett publikt dokument kan flyttas till Teams medans ett dokument utan klassificering (sensitivity label) blir blockerat för uppladdning.
Blockera enheter som saknar DLP stöd
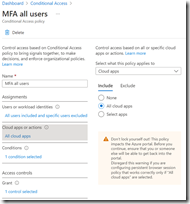
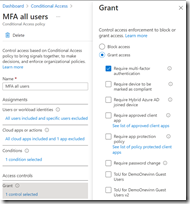
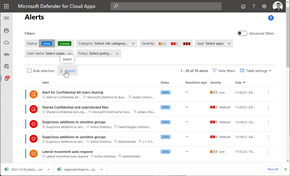
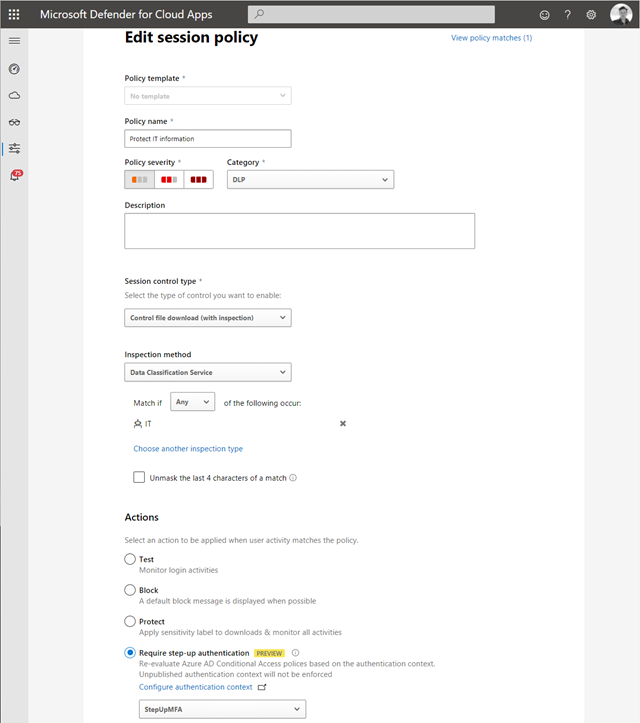
Med hjälp av Conditional Access säkerställer vi att det enbart är managerade klienter med denna DLP teknik som når M365 tjänster. Med hjälp av Defender for Cloud Apps kan vi ge en begränsad behörighet att enbart använda webb access för övriga enheter där vi blockerar upp/nedladdning baserat på likvärdigt regelverk.
Befintlig data
Finns det redan data lagrad i molnet som kan innefattas av dessa eller nya krav kan vi få logik i EndPoint DLP som helt enkelt flyttar information och lagrar den lokalt. Filen byts då ut av en text fil där vi kan/bör förklara VARFÖR den har flyttats och var användaren nu kan hitta informationen.
Som med all DLP funktionalitet bör det här användas med försiktighet. Blockerar vi våra användare/verksamheter utan att motivera varför och ger dom ett fungerande alternativ att utföra sina arbetsuppgifter ökar risken att de nyttjar helt andra tjänster att utföra sitt arbete och vi tappar kontrollen helt.
Rikets/Sveriges Säkerhet
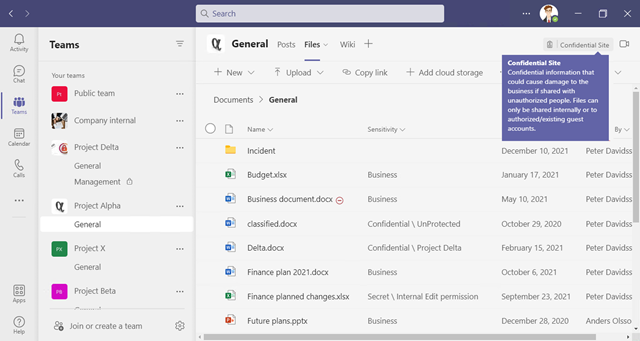
Flera av våra myndigheter har information som innefattas av informationsklassificeringen ”Rikets säkerhet”. Det här är information som hanteras i helt slutna system (eller i pappersform) utan någon form av internetanslutning. Den här typen av information ska/kan inte klassificeras med hjälp av sensitivity labels. Där emot är det viktigt att ha någon form av detektering OM den skulle förekomma i verksamhetens molntjänster.
Här finns det möjligheter att definiera upp standarder som används i dessa slutna system. Med hjälp av något som är identifierbart kan den här informationen detekteras och på samma sätt både förhindra att den laddas upp till molntjänster, flyttas till lokal lagring och larma om den identifieras på internetanslutna enheter.































![image_thumb[2] image_thumb[2]](https://svenskaforefront.files.wordpress.com/2021/07/image_thumb2_thumb.png?w=234&h=522) I have now been working for over 15 years with Microsoft security solutions and I have just been recognized as a Microsoft MVP (Most Valuable Professional) for the 11th year in a row.
I have now been working for over 15 years with Microsoft security solutions and I have just been recognized as a Microsoft MVP (Most Valuable Professional) for the 11th year in a row.


 Jag har nu jobbat i över 15 år med Microsofts säkerhetslösningar och jag har precis blivit utnämnd till Microsoft Most Valuable Proffesional, MVP för 11:e året i rad.
Jag har nu jobbat i över 15 år med Microsofts säkerhetslösningar och jag har precis blivit utnämnd till Microsoft Most Valuable Proffesional, MVP för 11:e året i rad.