Microsoft has just announced a public preview of adaptive protection within Data Loss Prevention (DLP).
What is this and why is this something important?
The main purpose of DLP is to increase awareness and prevent end-user mistakes. I would definitely not recommend to start a DLP journey by blocking users. The risk of preventing action on our business is not only angry/frustrated users but also that it can result in them finding other ways to do their work. Where so-called shadow IT results in company information being created, stored, and shared outside the companies IT environments.
The question is in what scenarios do we actually want to prevent and stop any possibility of leaking company information?
One example would be an insider risk where an internal user tries to leak internal secrets. Microsoft Purview Insider Risk Management is a great tool to identify these insider risks.
Adaptive protection is a new capability in Microsoft purview that uses AI and machine learning to dynamically protect data. Adaptive protection leverages machine learning analysis in insider risk management to detect risky user actions that may result in a data security incident. It automatically adds that user to a stricter data security policy such as a data loss prevention policy to block specific activity. This is great because the protection policies are adaptive based on user context ensuring that low risk users can maintain productivity and high-risk users have appropriate protection in place. Overall, this will help relieve part of the heavy burden of protecting data in a hybrid and rapidly changing environment.
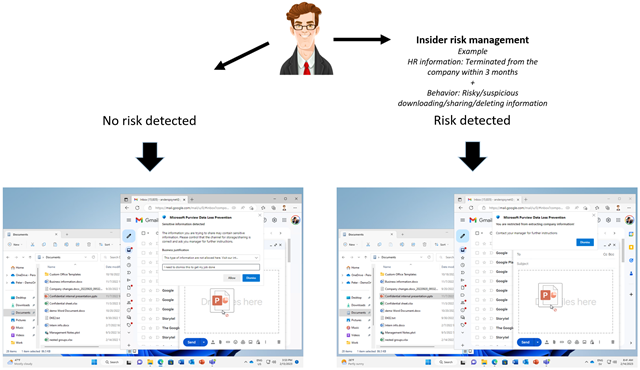
If we start looking at the end-user experience. Here we see that an internal user attaches company information into a private email account. Be default we notice the user about this kind of action, but the user can proceed and allow the action.
But if there is an identified insider risk with the user, the exact same action is being blocked without any way for the user to proceed.
How is this done?
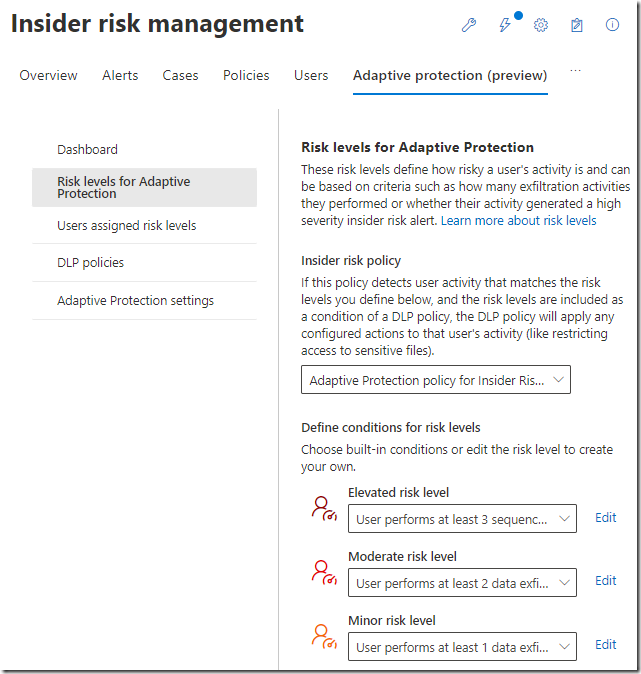
If we start looking at Insider Risk Management we have a new menu for Adaptive Protection. Here we can fine tune different risk levels, configure DLP policies and monitor this service.
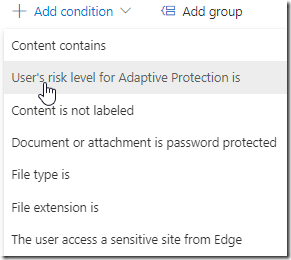
If we look at our DLP rules we see that we now have a new condition that can be added to our DLP rules. User risk level affect today DLP policies for EndPoint and Exchange.
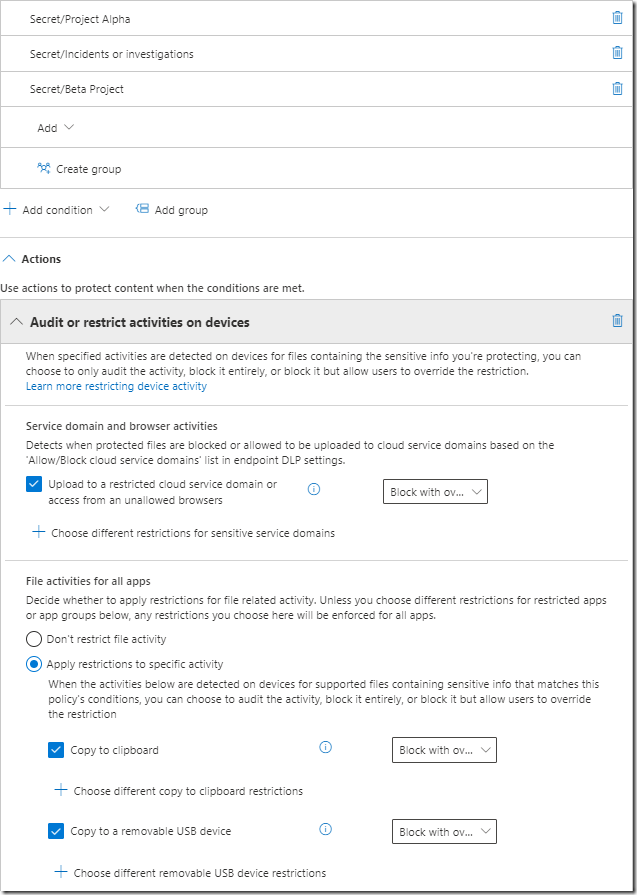
To achieve this scenario, we simple have two different DLP rules. The first one notify and recommend the end user if company information is extracted with Block with override.
The second rule include the same conditions and the User Elevated Risk level that simply block all actions.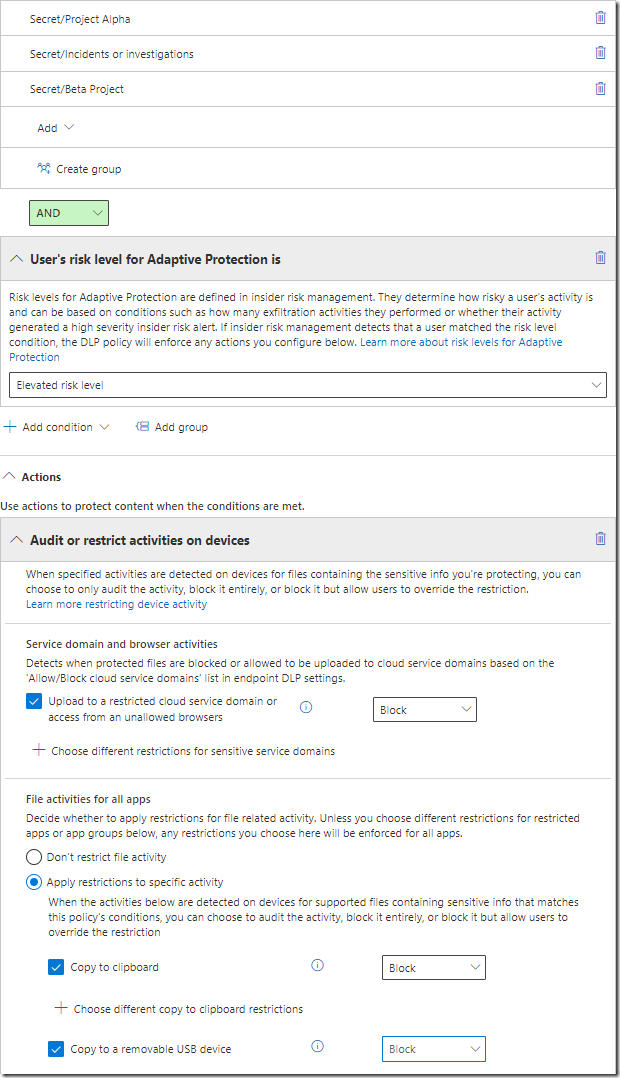
This shows that Adaptive protection in Microsoft purview combines the content centric controls from data loss prevention along with the people centric context from insider risk manager. This helps organizations balance data protection and productivity. Adaptive protection leverages machine learning to gain user context and insights about risky activities that may result in security incidents. It automatically tailors the controls based on risk detected so that organizations can enforce the most effective controls on the highest risk users, while everyone else works as usual.
Adaptive protection enables you to create more proactive and risk adaptive DLP policies so that organizations can contain exfiltration impact. Lastly it helps SecOps teams reduce alerts fatigue and the constant triage to identify the true risk. They can now protect more with less by leveraging the ongoing prioritization adaptive protection provides and it drives both effectiveness and efficiency.
Important: integrity within Insider Risk Management (IRM)
To maintain referential integrity, anonymization of usernames (if turned) isn’t preserved for users from Adaptive Protection who have alerts or activity appear outside insider risk management. Actual usernames will appear in related DLP alerts and the activity explorer.
Protect against external threats
Other actions that we normally use for our own playbooks is to combine DLP alerts with device or user behavior risks from Defender and AAD Identity Protection that isolate devices or block users. This is most common for external threats and in the same way preventing information leakage. In that case the compromised device is isolated, and nothing can be extracted from the device. A hijacked account is blocked, and nothing could be accessed (or shared) from that account.